Okta has recognized that it made a mistake by delaying the notification of a January attack by the Lapsus$ data extortion gang.
The corporation has also published a full timeline of the occurrence and its subsequent inquiry.
“We made a mistake,” Okta says of the late breach disclosure.
Okta apologized for not sharing data about the Lapsus$ hack sooner and provided a timeline of the incident and its investigation on Friday.
Sitel, Okta’s third-party provider of customer support services, was hacked by the Lapsus$ data extortion gang.
“The Okta Security team was notified on January 20, 2022, that a new factor had been added to a Sitel customer support engineer’s Okta account. It was a password that served as this factor “Okta explains.
“Although that individual attempt was unsuccessful, we reset the account and contacted Sitel,” says the company, which then hired a top forensic agency to conduct an investigation.
“We want to recognize that we made a mistake,” Okta says, adding that it bears ultimate responsibility for its outsourced service providers like Sitel.
Okta claims it was unaware of the scope of the event in January, believing it to be restricted to a failed account takeover attempt aimed at a Sitel support engineer.
Sitel’s hiring of a forensics firm to investigate the incident and prepare a report also assured Okta at the time that the situation didn’t need to be escalated any further.
“We didn’t realize there was a risk to Okta and our consumers at the time. Sitel should provide us with more actively and forcibly compelled information. Given the evidence we’ve gathered over the last week, it’s evident that if we’d had all of the facts we have now, we would have made a different conclusion “Okta agrees.
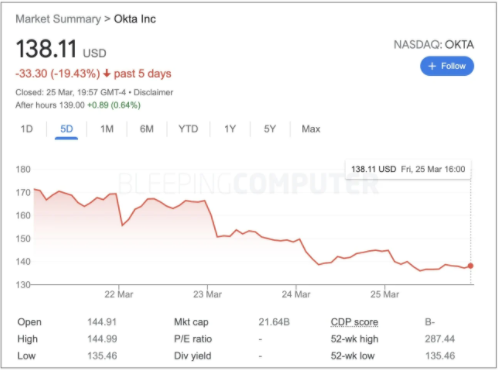
Following the news, Okta’s stock dropped over 20%.
The stock price of Okta dropped about 20% in less than a week after the company’s clumsy announcement of the January hacking incident:
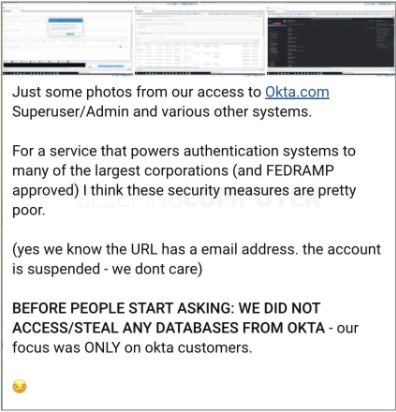
Okta has earlier indicated it was investigating reports of a hack when Lapsus$ members uploaded multiple screenshots in a Telegram chat claiming they had infiltrated Okta’s client networks, as reported by BleepingComputer this week:
At first, Okta CEO Todd McKinnon described the event as a “attempt” by threat actors to hack a support engineer’s account. However, it was eventually discovered that the problem had affected 2.5 percent of Okta’s clients, or 366 in total.
An attacker gained Remote Desktop (RDP) access to a Sitel support engineer’s laptop during the breach, which took place between January 16th and 21st.
According to Okta, Sitel’s support engineers have limited access to Jira requests and support systems, but they are not allowed to download, create, or delete client records.
“Support engineers can help users reset their passwords and multi-factor authentication factors, but they can’t choose those passwords,” Okta notes.
Support engineers, in other words, can constantly force password resets for users but are unable to log in to their accounts.
According to Okta, the screenshots posted by the Lapsus$ group were taken from a compromised Sitel engineer’s account with limited access.
The company further denied that Lapsus$ had gotten “superuser/admin” access, emphasizing that the access obtained by Lapsus$ was confined to an internal Okta support tool and was not the same as “superadmin” access, which grants full access to all users and system assets.
According to Okta, the application used by Sitel engineers is created with “least privilege” in mind, ensuring that support engineers have only the access they need to accomplish their jobs.
Regardless, the corporation voiced dissatisfaction with the length of time it took for the investigation’s findings to be released:
“I am deeply disturbed by the length of time between our notification to Sitel and the release of the full investigative report,” stated David Bradbury, Okta’s Chief Security Officer.
“Upon reflection, we should have moved more quickly to understand the significance of the Sitel summary report after we received it.”
Okta’s security specialists have had a busy week, reviewing over 125,000 log entries to come up with an authoritative picture of the cyber intrusion that occurred two months ago.
“There are numerous possibilities for us to improve our processes and communications, as there are with all security events. I’m certain that we’re on the right track, and this incident will only help to reinforce our security commitment “Bradbury comes to a conclusion.









