IcedID malware propagation has increased recently as a result of a new effort that hijacks existing email conversation threads and injects hard-to-detect malicious payloads.
IcedID is a modular banking trojan that was initially discovered in 2017 and is mostly used to distribute second-stage malware like other loaders or ransomware.
Its operators are thought to be initial access brokers who hack networks before selling the credentials to other crooks.
Researchers at Intezer identified the continuing IcedID effort earlier this month and shared their findings with Bleeping Computer before they were published.
The Attack’s Mechanism
The most common way of conversation hijacking is to take control of a key email account involved in a conversation with the target, then send a phishing message that appears to be a continuation of the thread.
As a result, the odds of suspecting fraud are reduced to a minimum when the target receives a reply message with an attachment labeled and presented as something related to the prior discussion.
Many of the affected endpoints they discovered are public-facing and unpatched, according to Intezer, indicating that threat actors are targeting weak Microsoft Exchange servers to collect credentials.
Furthermore, the researchers have seen malicious emails delivered through internal Exchange servers, utilizing local IP addresses within a more trustworthy domain, and hence unlikely to be flagged as suspicious, in this campaign.
As a result, the odds of suspecting fraud are reduced to a minimum when the target receives a reply message with an attachment labeled and presented as something related to the prior discussion.
Many of the affected endpoints they discovered are public-facing and unpatched, according to Intezer, indicating that threat actors are targeting weak Microsoft Exchange servers to collect credentials.
Furthermore, the researchers have seen malicious emails delivered through internal Exchange servers, utilizing local IP addresses within a more trustworthy domain, and hence unlikely to be flagged as suspicious, in this campaign.
Finally, the C2 sends a payload to the infected system, despite the fact that this step was skipped during Intezer’s investigation.
Campaign ties for November 2021
While Intezer’s analysis focuses on current and ongoing activities, the exact start date of this campaign is unknown. It’s probable that it’s been going on for five months.
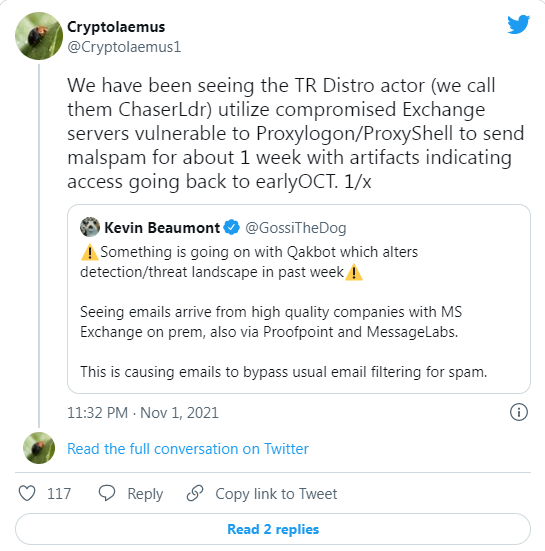
In November 2021, a Trend Micro study reported a surge of assaults that hijacked internal email reply-chains and transmitted malware-laced documents by exploiting the ProxyShell and ProxyLogon vulnerabilities in exposed Microsoft Exchange servers.
The perpetrators were thought to be ‘TR,’ who have been linked to a variety of viruses, including Qbot, IcedID, and SquirrelWaffle.
All three malware elements have been linked to the hijacking of email threads to deliver dangerous payloads in the past [1, 2, 3, 4].
The usage of regsvr32.exe for the DDL’s binary proxy execution and password-protected ZIP files puts threat group TA551 in the limelight this time, according to Intezer.
The link between those two danger groups is unknown, but there’s a good chance there’s some overlap or possibly an underlying connection.
Your Exchange servers should be updated.
Since Microsoft released remedies for the ProxyLogon and ProxyShell vulnerabilities over a year ago, it’s a pastime to install the most recent security upgrades.
If you don’t, phishing actors, cyber-espionage, and ransomware attacks will target your Exchange servers, firm, and workers.