DDoS assaults against a dozen Russian and Belarusian websites managed by government, military, and press organizations were carried out using Docker images with a download count of over 150,000.
Pro-Ukrainian actors, such as hacktivists, are suspected of being behind the incidents, which are likely sponsored by the country’s IT Army.
DDoS cyberattacks try to paralyze operations by flooding the target with more requests than it can process, rendering it unavailable to legitimate clients.
Docker APIs as a target
The Russian government, Russian military, and Russian media, including as the TASS news agency, are among the 24 domains attacked.
Threat researchers at cybersecurity firm CrowdStrike discovered two Docker images used in the assaults, which were distributed in February and March 2022.
Cryptocurrency mining gangs like Lemon Duck and TeamTNT have been targeting open Docker APIs for years.
Unfortunately, there are a lot of misconfigured or poorly protected Docker deployments out there, which allows threat actors to take advantage of the available resources.
CrowdStrike discovered that two malicious images fetched directly from the Docker Hub repository had infected its honeypots with exposed Docker Engine APIs.
The DDoS attack targets were initially chosen at random, but later versions of the images included a time-based selection and a hardcoded list of targets that were struck in one-hour assaults.
CrowdStrike believes that this campaign is likely funded by the Ukraine IT Army or similar hacktivists, based on the nature of the operation and the scale of the targeting.
The use of DDoS assaults may provoke retaliation by pro-Russian hackers, resulting in a lengthy and damaging service outage.
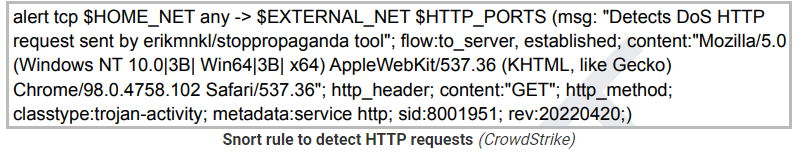
CrowdStrike has published the following Snort rule to assist administrators in detecting unauthorized activity: